Best VPNs Based on In-Depth Reviews
- 160+Hours of research
- 47+Sources used
- 22Companies vetted
- 4Features reviewed
- 4Top
Picks

- Nearly all VPNs collect some type of log information
- VPNs can improve security while using public Wi-Fi
- Using a VPN will not make you anonymous
- VPNs tend to slow connection speed
How We Found the Best VPNs
Our Top Picks: VPN Reviews

The virtual private networks (VPNs) we considered and reviewed are known as commercial remote access VPNs. These tunnel your traffic from remote servers to their private network and then to its eventual destination. Exactly how this is done depends on the protocol they employ, but the end result is essentially the same: the data arrives at its destination under the guise of a different IP address than your own.
VPNs are not a comprehensive solution to consumers’ online security and privacy concerns. That’s why all the VPNs featured on this list offer some method—other than reading their privacy policy—of verifying that they keep minimal or no logs.
We also focused on selecting VPNs that would benefit specific user groups.
NordVPN Review:
NordVPN is a leading VPN service renowned for its robust security features, extensive server network, and user-friendly interface. It caters to privacy-conscious individuals, gamers, and streamers, ensuring secure and private internet access across various devices.
Key Features:
- Encryption and Security: NordVPN employs next-generation encryption protocols, including its proprietary NordLynx technology, to safeguard user data. Features like Threat Protection Pro™ and Dark Web Monitor enhance online safety by blocking malicious websites and monitoring for data breaches.
- Streaming and Privacy: With over 5,200 servers in 60 countries, NordVPN effectively bypasses geo-restrictions, allowing access to various streaming platforms. Its strict no-logs policy ensures that user activity remains private.
- Speed and Performance: NordVPN offers high-speed connections with unlimited bandwidth, utilizing advanced technologies to maintain optimal performance without compromising security.
- Compatibility: NordVPN is compatible with Windows, macOS, Linux, Android, iOS, and various browsers, providing dedicated apps and extensions for seamless integration across devices.
- Number of Devices: A single NordVPN account can protect up to 10 devices simultaneously, making it suitable for individuals and families.
- Optional Add-Ons: NordVPN offers additional services like NordPass, a secure password manager, and NordLocker, an encrypted cloud storage solution, enhancing overall cybersecurity.
Server Network:
NordVPN boasts a vast network of over 5,200 servers in 60 countries, providing users with a wide range of options for secure and private internet access.
NordVPN Price and Plans:
NordVPN offers flexible pricing plans, including monthly, annual, and two-year subscriptions. Prices vary depending on the selected plan and any ongoing promotions. A 30-day money-back guarantee is available, allowing users to try the service risk-free.
Best For Streaming
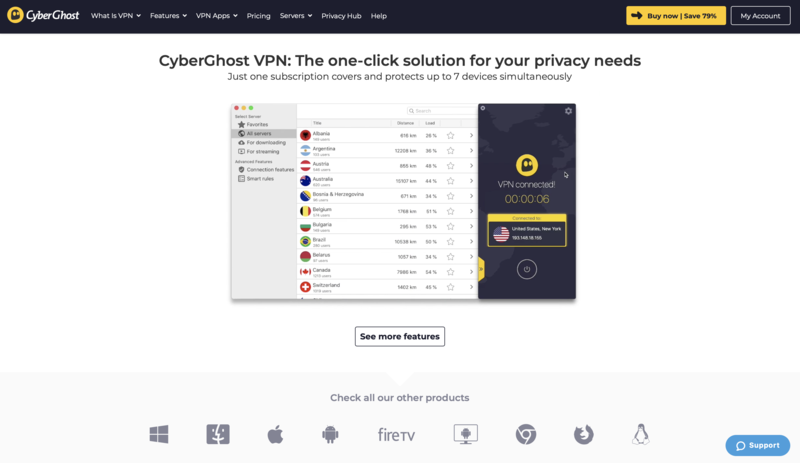
Screenshot cyberghostvpn.com, January 2020.
IP addresses used by VPNs are constantly getting blacklisted by streaming services. For some VPNs—especially those whose main focus isn’t entertainment—it takes longer to develop workarounds to gain access again. VPNs that focus on streaming, like CyberGhost, can dedicate its resources to this issue and are more capable of ensuring that its servers will have access to popular streaming options.

Screenshot cyberghostvpn.com, January 2020.
CyberGhost was one of only two VPNs we considered that has dedicated servers for streaming. We found that the service allowed us to access Netflix US, Netflix UK, Hulu, SlingTV, BBC iPlayer, and HBO Now.
What stood out:
- CyberGhost has the highest number of servers among all the VPNs we looked at. On their website, they currently list 6,178 servers in 108 locations across 88 countries. This network density allows for much higher volumes of Internet traffic, almost ensuring that users don’t experience significant slowdowns.
- In addition to dedicated streaming servers, CyberGhost also features dedicated servers for peer-to-peer (P2P) connections.
- Compared to other VPNs operating in countries outside the Five Eyes jurisdiction, CyberGhost is much more transparent. The company openly discloses its leadership and corporate structure and was the first VPN in the industry to publish a transparency report.
- CyberGhost was one of the ten VPNs tested in 2019 by AV-TEST, an independent research institute that evaluates IT security solutions. It received the institute's seal of approval, which certified it as an Approved VPN Solution.
Letdowns:
-
CyberGhost’s speeds were middling. They weren’t terrible but did not impress us for a service that is focused on bandwidth-heavy activities like streaming. Speeds were consistent, though, likely as a result of its high server count.
No No’s:
- Out of all the VPNs we tested, CyberGhost has one of the least intuitive app interfaces. The server’s window is cumbersome to navigate and noticeably slow.
- At $12.99/mo, CyberGhost is the most expensive product among all the VPNs we looked at.
🏅Rated #1 VPN in Overall Performance
Norton VPN Review:
Norton Secure VPN, offered by the trusted Norton brand, provides robust online privacy and security for everyday users. Norton protection is designed for privacy-conscious individuals, gamers, and streamers, protecting your data on public Wi-Fi and ensuring anonymity with its no-log policy.
Key Features:
- Encryption and Security: Norton Secure VPN uses bank-grade AES-256 encryption to safeguard data.
- Streaming and Privacy: Norton Secure VPN supports streaming platforms like Netflix and Hulu but lacks specialized servers for torrenting. Norton VPN operates under a no-log policy, ensuring user data isn’t stored.
- Speed and Performance: Ranks #1 for overall network performance¹ with upload and download speeds nearly 2.5x faster than the average VPN, outperforming competitors.
- Compatibility: Norton security is compatible with Windows, macOS, iOS, Android, routers, etc.
- Number of Devices: Protect up to 10 devices with Norton Ultra VPN Plus.
- Optional Add-Ons: Norton Ultra VPN offers essential tools like a Password Manager, Dark Web Monitoring, LifeLock 360 Antivirus, Ad Blocker, Parental Control‡, and up to 50 GB of Cloud Backup.²
Server Network:
The Norton VPN app provides servers in 28 countries so you can enjoy what you’re doing more securely, privately, and without interruption.
Norton VPN Price and Plans:
Norton VPN cost is affordable, with plans starting at $9.99/month for the first year—with annual, multi-year and family plan options available. The Norton VPN download offers a 60-day money-back guarantee, allowing risk-free trials for new users.
Surfshark VPN Review:
Surfshark VPN is a comprehensive cybersecurity solution offering robust online privacy and security. Designed for privacy-conscious individuals, it provides advanced features to protect your data across multiple devices, ensuring anonymity with its strict no-logs policy.
Key Features:
- Encryption and Security: Surfshark utilizes AES-256-GCM encryption and supports secure protocols like WireGuard®, IKEv2, and OpenVPN to safeguard your data.
- Streaming and Privacy: Supports streaming platforms such as Netflix and BBC iPlayer, allowing access to geo-restricted content. Surfshark operates under a strict no-logs policy, ensuring user data isn’t stored.
- Speed and Performance: Offers high-speed connections with over 3,200 RAM-only servers in 100 countries, providing a seamless browsing experience.
- Compatibility: Compatible with Windows, macOS, iOS, Android, Linux, routers, and smart TVs, ensuring protection across all your devices.
- Number of Devices: Allows unlimited simultaneous connections, making it ideal for individuals and families with multiple devices.
- Optional Add-Ons: Surfshark offers additional tools like Antivirus, Alert (data breach monitoring), Search (private search engine), and Alternative ID to enhance your online security and privacy.
Server Network:
Surfshark provides over 3,200 RAM-only servers in 100 countries, allowing you to enjoy secure and private browsing without interruption.
Surfshark VPN Price and Plans:
Surfshark offers affordable plans, with subscriptions as low as $2.19 per month for a two-year plan. All plans come with a 30-day money-back guarantee, allowing risk-free trials for new users.
Best for Small Teams

Screenshot windscribe.com, January 2020.
Windscribe is another excellent choice for business if your needs do not include remote access to company resources. Consider, for example, a group of researchers in your business who need to see search results from other parts of the world. Windscribe’s team accounts, called ScribeForce, function on a flat rate of $3. They include all the features of a paid Windscribe account with added centralized billing and a team management panel.

Screenshot windscribe.com/scribeforce, January 2020.
A very efficient VPN, Windscribe tackles issues of online privacy and security on two fronts simultaneously. In addition to solving problems VPNs are usually employed for, Windscribe includes an all-in-one, ad, malware, malicious website, and tracker blocker called R.O.B.E.R.T. It also functions as a domain whitelister and can block websites that fall under specific categories, such as gambling, social network, and fake news + clickbait.
What stood out:
- The price disparity between regular and team accounts. ScribeForce accounts are so inexpensive, that five of them (the minimum to apply for the service) are less expensive than two regular accounts.
- Windscribe uses a firewall for its connections rather than a kill switch. As explained below, firewalls are a vastly better alternative than kill switches, which most over VPNs employ.
- A limited version of the Windscribe client is free to download. This lets users take a test run of the service before committing to an actual purchase.
Letdowns:
- Speeds on Windscribe weren’t the fastest. They landed right in the middle of the 15 VPNs we tested, speed-wise.
- Windscribe has a relatively low number of servers when compared to major competitors.
Total VPN Review:
Total VPN offers comprehensive online privacy and security solutions for users seeking to protect their digital footprint. With advanced encryption protocols and a user-friendly interface, it ensures that your internet activities remain private and secure across various devices.
Key Features:
- Encryption and Security: Utilizes military-grade encryption to safeguard your data, ensuring anonymity and protection from cyber threats.
- Streaming and Privacy: Access geo-restricted content effortlessly with over 50 super-fast servers in more than 30 countries, providing uninterrupted streaming and browsing experiences.
- Speed and Performance: Optimized for speed, Total VPN allows for seamless streaming, downloading, and browsing without lag or interruptions.
- Compatibility: Available on Windows, macOS, iOS, and Android platforms, ensuring protection across all your devices.
- Number of Devices: Protect up to 5 devices simultaneously, making it suitable for both individuals and families.
- Optional Add-Ons: Includes free antivirus protection and an ad blocker, enhancing your overall online security and browsing experience.
Server Network:
Total VPN boasts a global server network with over 50 super-fast servers in more than 30 countries, allowing users to access their favorite content securely and without interruption.
Total VPN Price and Plans:
Total VPN offers an affordable plan at $1.59 per month, which includes free antivirus protection and an ad blocker. A 30-day money-back guarantee is provided, allowing users to try the service risk-free.
Best For Privacy and Security

Screenshot mullvad.net, January 2020.
If there’s one VPN that defines “show, not tell” in the realm of security, it’s Mullvad. The company’s commitment to your privacy can be seen from the moment you sign up. Instead of a traditional account with a name and email address, users simply get a code that is linked to their account. Payment follows this trend towards privacy, with options for bitcoin, vouchers, and cash.

Screenshot mullvad.net, January 2020.
Mullvad’s privacy policy is clear and easy to understand. It clearly states how they handle payments and user reports, the data they log—which is almost none at all—and how its numbered accounts work. Moreover, Mullvad is an early adopter of the WireGuard protocol. Although still considered a work-in-progress, the protocol has received much praise for its highly secure connections and excellent speeds.
What stood out:
- The minimalist desktop client. Mullvad’s app never even opened a separate window, managing all of its essential functions on its tab interface.
- Speeds on Mullvad weren’t the fastest, but they still beat more than half of the VPNs we tested. Establishing connections was also remarkably fast.
- The low price. The company has a single payment option, €5/mo (approx. $5.50/mo), which is the lowest among all the VPNs we considered.
Letdowns:
-
Mullvad has a lower number of servers and server locations than many of the VPNs we looked at.
No No’s:
-
There’s no “one-click method” to get Mullvad working on mobile devices. The process requires some setup that ordinary consumers might not feel confident doing.
Best For Privacy Bundle

Screenshot protonvpn.com, January 2020.
Although VPNs are a strong tool for enhancing your online privacy and security, they can’t protect you in every situation. One common mistake people make is going into their free mail provider—Gmail, for instance—with their VPN on, expecting that Google won’t be able to see what they are doing. Later, when they are targeted by ads related to the content in their emails, they are shocked to find out that they were indeed used to track them.
ProtonVPN is a robust, affordable, and versatile VPN by itself. By bundling it with CERN’s original product, ProtonMail, consumers can enjoy even greater peace of mind knowing that their email is under greater protection.

Screenshot protonvpn.com, January 2020.
ProtonMail’s main selling point is its end-to-end encryption. When sending email to non-ProtonMail users, the recipient gets a link which loads the encrypted message onto their browser. They must then use a passcode to access the email. ProtonMail users can also set messages to self-destruct, and their anonymity is ensured since Proton does not save any tracking information—and they couldn’t, even if they wanted to—since they can’t read your mail.
What stood out:
- ProtonVPN has four price tiers. Higher tiers introduce a greater number of simultaneously connected devices, greater speeds, more server locations, and premium servers.
- ProtonVPN uses ciphers with Perfect Forward Secrecy. This means that traffic cannot be captured and decrypted later, even if it’s compromised in the future.
- On January 21st, 2020, all ProtonVPN apps went open source. Any software that is open source benefits from enabling anyone to look for and fix security flaws. By sharing their code with the world, open source software also fosters greater trust and transparency.
- ProtonVPN is supported by the Horizon Framework Programme of the European Union, the biggest EU Research and Innovation program to date.
- The Secure Core Network, a ProtonVPN feature, helps defend against network-based attacks by routing your traffic through multiple servers located in Switzerland before leaving Proton’s network.
- Users can create “profiles” in the ProtonVPN client. These profiles let users customize different types of connection for easy access.
Letdowns:
- In the client, users can search for servers by country name but not city name.
- ProtonVPN has less servers than other, more popular VPNs. This shows to a degree; during our time testing the service, barely any of its servers had low traffic.
No No’s:
-
At first sight, it looks as if the only bundling option is on the Visionary tier, which is a whopping $30/mo. This is somewhat misleading. You can actually bundle any ProtonVPN plan with any ProtonMail plan for a discount.
🏅Best All-In-One Digital Bundle
Norton 360 Deluxe Review:
Norton 360 Deluxe is an all-in-one cybersecurity solution offering powerful antivirus protection, secure VPN, password management, and dark web monitoring. Designed for individuals and families, it provides advanced security features to safeguard personal devices against malware, ransomware, and phishing attacks while ensuring online privacy.
Key Features:
- Advanced Security: Norton 360 Deluxe uses real-time threat protection with AI-driven security to defend against viruses, spyware, and emerging cyber threats.
- Secure VPN: Includes a no-log VPN with bank-grade encryption to protect your online activity and personal information on public Wi-Fi.
- Dark Web Monitoring: Alerts users if their personal information, such as email addresses and passwords, is found on the dark web.
- Cloud Backup: Provides 50GB of cloud storage to help prevent data loss due to ransomware or hardware failure.
- Parental Controls: Helps parents manage their children’s online activities with content filters and screen time limits.
- Device Compatibility: Works on Windows, macOS, Android, and iOS devices.
- Multi-Device Protection: Covers up to 5 devices, making it ideal for families or individuals with multiple devices.
Performance and Reliability:
Norton 360 Deluxe is known for its minimal impact on system performance while running scans and updates. It consistently ranks among the top security suites in independent tests for malware detection and protection.
Norton 360 Deluxe Price and Plans:
Norton 360 Deluxe is available at an introductory price of $49.99 for the first year, covering up to five devices. The subscription includes a 60-day money-back guarantee, allowing users to try the service risk-free.

Further Insight into Our Methodology
VPNs used to be a niche product until just recently. Now widely available, they are a powerful tool for people who want to enhance their online privacy—to a degree. They can, for example, help access geo-restricted content, bypass censorship, and keep your online activity private from your internet service provider (ISP). They cannot, however, make you 100 percent anonymous or keep your data encrypted after it leaves their servers.
As the personal use of VPNs has increased, so has the number of VPN products available online. Many of them claim similar feats regarding their service and features, which leads us to the question: How does one choose the best VPN?
We scoured the web for resources, spending more than 160 hours researching the technology of VPNs, as well as their uses, limitations, benefits, and pitfalls and we ultimately decided on four factors for evaluating VPNs, which are listed below in order from most to least significant.
Security & Privacy
Security and privacy are the main selling points of VPN services. Even when using one for entertainment purposes, for example, it’s the effect of obfuscating your IP address that makes a VPN valuable. Transparency and commitment to keeping any data they retain from you at a minimum are what separates the good VPNs from the bad.
VPNs are in a privileged position when it comes to your personal information. By using them, you are essentially shifting the focus of trust from your ISP to them. The VPN becomes your new data custodian. We favored VPNs that provided a clear explanation of their logging practices in their privacy policy.
After checking policies, we looked at two other elements that show transparency in a VPN. The first was transparency reports, which are generally published on a regular basis and include information about the company, such as the number of data quests and government warrants. This type of document isn’t exclusive to VPN companies; all types of businesses can benefit from a transparency report.
The second element is third-party audits. This is when a VPN hires a tech firm to inspect their code and, sometimes, server infrastructure. For a VPN, an audit can help identify both minor and key faults of their service that need improvement. For consumers, an audit shows that the VPN is willing to subject itself to scrutiny from experts.
Another thing we considered was legal jurisdiction. We had initially favored VPNs based in countries outside of the Five Eyes / Fourteen Eyes intelligence alliance(s) believing that, for those that wanted the most guaranteed level of privacy, this was the way to go. As we continued our research, however, we realized this was not necessarily the case. If a government or another large entity knew you used a VPN and wanted to get their hands on your log information, there is little you'd be able to do about it. Instead, we ended up favoring local and E.U.-based VPNs.
In the U.S., local VPNs are subject to a high level of scrutiny regarding their data practices. E.U.-based VPNs, for their part, are required to comply with the General Data Protection Regulation (GDPR), which ensures companies doing business in the European Union are held to a high standard of transparency when it comes to personal data retention and use.
Finally, we considered any extra methods VPNs employ to keep users secure while they use the product. This includes features such as multi-hop connections—which slow speeds but add another layer of misdirection—and obfuscated servers, which conceal the fact that you are using a VPN.
Performance
When you use a VPN, data leaves your personal network, is encrypted and tunneled in and out of the private VPN network, and finally arrives at its destination after traveling the remainder of its path through the public Internet. Your internet speed inevitably slows down, and the farther away from the server you connect to, the slower your connection is likely to be. VPNs are often finding ways to outdo one another by providing faster, more consistent connections.
We originally considered using numbers from third-party sources to determine the best-performing VPN. This turned out to be unviable; the only source of information available was the Speedtest’s 2019 Fastest VPN Awards. Thus, we decided to run our own tests on the 15 VPNs that made our cut, from the original list of 22.
We ran speed tests for each of the 15 VPNs on five different servers. To cast a wide geographical net and test for speeds at different distances from our local servers, we used servers located in New York, London, Tokyo, São Paulo, and Sydney. We also ran tests for Johannesburg, but because at least half of these services did not have a server there, we ultimately didn't consider their numbers in the final tally.
Not all speed test tools are built the same, which results in conflicting results—even if tests are performed at the same time and location and under the same circumstances. We ran our tests using Ookla’s Speedtest and Google’s Measurement Lab (M-Lab) tools. The former often provided ideal performance numbers, while the latter tended to understate connection performance. This gave us a wider range of numbers to work with and report on. Sadly, M-Lab failed to give us results on a wide variety of servers and services. Therefore, we ultimately decided to exclude its results from our final numbers, given their irregularity.
Since running speed tests at different times of day produce different results, just testing for location wasn’t enough. This is the result of Internet traffic, which is a constant variable. We decided the same test would be undertaken twice: once in the morning and once in the afternoon.
Two of our researchers undertook the task of testing during the span of two workdays. They ran tests on Friday and Monday from 9 a.m. to 12 p.m. and 2 p.m. to 5 p.m. One of our researchers ran tests on Windows and the other on macOS to test for any differences between the two operating systems. Both speed testing tools were used on Google Chrome to eliminate any variables regarding web browsers.
Our goal was to run a total of 720 speed tests—360 of those were discarded or unable to be completed due to inconsistencies with M-Lab and 120 were disregarded or incomplete due to the lack of servers in South Africa for many VPNs. Ultimately, we favored VPNs with lower latency and higher Mbps that showed less of an impact on our server tests.
Cost
The vast majority of VPNs are subscription-based products. A limited number do offer one-time (i.e. lifetime) purchases of their product, but we urge you to avoid these for several reasons. Common pricing methods among VPN companies include monthly payments, yearly payments, and multi-yearly payments (two, three, or even five years). Some companies have three-month and six-month payment cycles as well. Only a single VPN on our list did not have a monthly payment option.
Another aspect of cost is bundling. Although not common, a few VPNs offer additional services with their flagship product. We only considered “bundled” services as those that are sold independent of the VPN or would be sold that way based on the type of product.
Money-back guarantees did not have a major impact on our final ratings, but we did highlight VPN providers that offer longer-than-average guarantees, such as 30 or 45 days after the date of purchase.
Features
We considered "features" as all the things advertised by VPN providers. One of the first things consumers are likely to see promoted is the number of servers used, which goes hand in hand with the number of individual IP addresses featured. The more servers a VPN has, the less likely it is that users will experience noticeable slowdowns. Therefore, we favored VPNs with a higher number of servers. The number of server locations is usually listed as a big selling point as well, but for different reasons. Having more server locations, particularly in different countries, makes it possible to access a wider variety of content that would otherwise be geo-blocked.
All-in-one malware, ad, and malicious website blockers are other common features among popular VPNs. These are usually included with the cost of a subscription, although some VPNs may charge extra. The same goes for whitelisters and tracker clearers (e.g. cookie cleaners). Kill switches would fall into this category, but we decided not to consider them. Instead, we favored the few VPNs that make use of firewalls to consistently protect from data leakages. Kill switches have a big flaw, namely that they are reactive—not proactive—safety measures. Having a kill switch is better than nothing, though.
One of the most important features we evaluated is the variety of protocols available for use. Protocols are the set of rules that VPNs use to make your information secure. They also have an impact on your VPN’s performance. Since protocols vary in performance and security level, we favored VPNs that support those which are considered the safest and fastest by the cybersecurity community. This includes, but is not limited to, IKEv2, WireGuard, and OpenVPN.
Helpful Information About VPNs
Commercial virtual private network (VPN) services have boomed in recent years. Originally designed for use in the business sector, VPNs are now being widely sought out by consumers. In 2019 alone, they accounted for 480 million of all mobile app downloads worldwide. Estimates say that the global VPN market could be worth more than 35 billion U.S. dollars by 2022 or even as much as $50 billion by 2024.
Outside the U.S and Europe, this growth is mainly attributed to the desire for more access to better entertainment content. In regions such as Asia and Latin America, being able to watch content that is geographically restricted trumps all other motivators for using VPNs. This is also a driving force in the U.S. VPN market, but the adoption of the technology here is no doubt a result of our growing concerns about personal privacy online.
Sadly, the way that VPNs are marketed can easily mislead consumers, giving them a false sense of security. Consumers in the U.S. who use VPNs are as likely to do so for entertainment purposes as they are for privacy and security reasons. The issue here is the latter; consumers are not always well informed about how and in what cases a VPN can bolster their privacy online.
How Do VPNs Work?
VPNs create virtual tunnels through which they channel your traffic into their private network. The connection to and from their network is usually protected by encryption technology. From there, the VPN throws your data back into the public Internet, where it eventually reaches its original destination. By the time that's happened, your data has arrived under the guise of a different IP address.

Simply put, VPNs work via misdirection. By rerouting your Internet traffic through its servers in a location other than your own, VPNs can effectively mislead anyone who is trailing you based on your IP address. This includes your ISP, which will only be able to see that you are using a VPN, and anyone snooping on you over public Wi-Fi. This is also how VPNs mislead streaming services, which are led to believe that a user is located in a specific region based on their IP address.
To move your data from your network to theirs, VPNs employ tunneling protocols–or communication protocols–which are the sets or standards of rules, syntax, semantics, and other elements that allow two devices to interact. They are a language of sorts; if two devices speak the same language, they may communicate.
In most cases, protocols also encrypt your data during transit. VPNs currently use several protocols of this type, including PPTP, SSTP, L2TP, IKEv2/IPSec, OpenVPN, and WireGuard.
What Can VPNs Do? What Can’t They?
VPN technology was designed for businesses so that employees and branch offices could have remote access to resources in their corporate servers. It was not made with everyday denizens of the Internet in mind, whose uses for VPNs differ drastically. Despite this, a combination of (ironically) misleading advertising and general misinformation has contributed to an idea that this technology can also do for the latter group what it does for the former.
This couldn’t be further from the truth.

Consider the issue of encryption. As we mentioned, VPNs are only able to safeguard the connection they establish between two private servers—yours and theirs. It makes sense, for example, that an employee working from abroad would be asked to use a VPN in order to keep the assets in their corporate servers secure and away from prying eyes. For regular consumers, though, this sort of protection doesn’t have as much value.
In a comprehensive 2019 article about VPNs, Dennis Schubert, a Superglue Engineer at Mozilla, illustrates what VPN encryption actually does. Working under the assumption that your connection is not encrypted beforehand—an assumption that he quickly shatters a bit further into the article—he created an illustration showing how a VPN can only do so much to protect your information online.
If you send unencrypted data over the internet, you are essentially sending out a love letter on the back of a postcard - Dennis Schubert, Superglue Engineer at MozillaHe then compares that to what sending data over the Internet while using a VPN looks like. His illustration barely changes from the original.
“Remember when I earlier described VPNs as a tunnel?” he asked. “Every tunnel needs to end somewhere… […] VPN providers are unable to deliver your data packets directly to the final destination because they do not actually know where that is.” He finished by stating that “All they can do is to throw your packets back into the public internet so that it eventually can reach its goal.”
In other words, unless your destination on the Web supports an encrypted connection, your data is vulnerable as soon as it leaves the VPN’s network.
In addition to encryption, anonymity is another often-misunderstood element of VPNs. A VPN cannot make you entirely anonymous online. And it is a misconception that you won’t be able to be tracked just by changing your IP address. In reality, tracking companies have developed numerous methods to keep their eyes on you; just changing your IP address won’t mislead them from your trail.
So, if a VPN can’t encrypt your data beyond its server walls and can’t keep you anonymous on the web, what can a commercial VPN do?
Leo Notenboom, a software writer with over forty years of experience who runs a popular online tech support resource, mentions three specific problems that VPNs can solve in one of his posts about VPNs. The first is sniffing, which is when a person uses the same Wi-Fi network as you to snoop on your Internet traffic. This is one problem that VPN encryption can solve. Because your data is encrypted up to when it’s sent into the public Internet, it’s safe from “sniffers” within range of your network.
The second has to do with relocation. When VPNs route your traffic through their network, it masks your IP address with one from another location. This is what lets users bypass the geographic restrictions placed on popular streaming services and access local channels unavailable abroad.
The third and final problem VPNs can solve is surveillance. When using a VPN, the same encryption that protects you from sniffers also hides information from your ISP. However, Notenboom did make a point that this problem is not entirely solved by VPNs. Your activity online can still give you away, especially if trackers, such as cookies, latch onto you during your time online. Furthermore, your VPN can now potentially monitor your activity online instead of your ISP.
What’s the Deal with Logs?
The terms “logging” and “logless” are thrown around liberally when talking about VPNs. Logs are the records generated by your online activity. They can be roughly split into two groups: metadata logs and traffic logs. Metadata logs include data that can help VPNs optimize their service (e.g. bandwidth consumption, timestamps) and are mostly harmless to collect. Traffic logs, on the other hand, reveal your browsing history, DNS requests, and real IP address, which a VPN should never keep.
Logs are important because they tell a story. Consider, for example, that your ISP is likely monitoring your browsing habits. They can use that information to build your personal profile, sell your data to third parties, and even throttle your bandwidth if they don’t agree with the content you are looking for. That’s why a VPN that does not keep your data secure is nothing more than a fancy gateway. VPNs that keep extensive logs, or worse, give them up freely to third parties are nothing more than glorified mini-ISPs.
Having said that, how does one verify that a VPN keeps minimal or no logs? By reading the company’s privacy policy, for starters. The document should disclose exactly what data the VPN gathers from its users, namely what logs it keeps and what it does with them.
One way to substantiate a VPN’s approach to log-keeping is by checking if they have a history of publishing transparency reports. A transparency report is written to showcase how transparent a given VPN is with its customers and the Internet at large.
The most surefire way of verifying what exactly a company does log-wise is by reviewing any third-party audits they have participated in. These are commissioned by VPN companies to identify potentially dangerous gaps in their code. However, audits aren’t guaranteed to prove a company keeps no logs, either.
Ultimately, consumers must always exercise a bit of faith when doing business with a VPN. There is no way of being 100% certain that they do not keep some log information, other than its servers being seized and investigated. Moreover, if one does not have faith that their VPN is being judicious and truthful about their policy regarding user data, then it makes no sense to shift the trust from one party—your ISP—to another—the VPN.
What to Watch Out for With VPNs
Kill Switches vs. Firewalls
Kill switches are one of the traditional VPN features that many services like to advertise. They function as an emergency stopgap that can automatically cut the flow of data in the event of a data leak. Kill switches are certainly useful and better than having no other “emergency escape pod” measure if your connection is interrupted. But unlike firewalls, they are unable to safeguard your connection at all times.
VPN firewalls are very much like those you can find active on your computer. They maintain the security of a private network—the VPN’s network, in this case—by protecting its connection from unauthorized or malicious interception. They are also a reactive measure; they act after the fact but are unable to stop packets of data from leaking out of the VPN’s established connection. Firewalls are proactive; while a VPN firewall is active, your data simply stops mid-transit in the case of an interruption.
Red Flags Regarding Free VPNs
As a rule of thumb, we advise consumers to steer clear of free VPNs. The only exception to this is some freemium VPNs. Of these, we only recommend trying out Winscribe and TunnelBear. We researched and tested both of these services, concluding that both run reputable businesses. There are several reasons why you should steer clear of free VPNs, but the most obvious is a direct result of the lack of regulation in the industry. VPN products are not required to follow any standards, which is why so many new, free ones regularly crop up in the Google and Apple stores. Free VPNs may track you, sell your traffic, throw advertisements in your face, and even include malware in their design.
A 2016 analysis of permission-enabled apps on Android showed several damning results regarding free VPNs. Only 28% of the free VPN apps analyzed in the study did not have any tracking library embedded, compared to 65% of premium VPN apps. They linked these numbers to free VPNs’ higher reliance on revenue from advertising and analytics services. Worse yet, 75% of the free VPN apps that claimed to protect users’ privacy included at least one tracking library. Moreover, free VPNs just don’t have the infrastructure to satisfy consumer demands.
Lifetime Subscriptions
There are a few VPN providers that offer lifetime subscriptions. We urge you to completely disregard these types of sales tactics. Consider that the company offering the VPN might close its doors one day. This more than likely means that their service will cease to function. Paying large sums of money in bulk for a subscription you might not get to fully enjoy isn’t the best idea. But even then, why tie yourself to a single VPN for a lifetime? Technology is always improving, and by paying for a lifetime subscription, you are essentially tying yourself to a VPN just because you paid for it.
VPN Glossary
DNS: the Domain Name System (DNS) is tasked with taking domain names, such as consumersadvocate.org and google.com, and translating them into IP addresses, which web browsers use to find resources on the Internet.
Encryption: a message is encrypted when it is secured through code in a way that only authorized parties can access it. This is done through an algorithm that generates an encryption key. Only those with a decryption key can easily access the message or information.
Geo-blocking: certain geographic regions are unable to experience Internet content present in others. The reason why companies and businesses prominently, streaming services—restrict content in some regions but not others are many.
IP address: every device on a network is assigned an Internet Protocol (IP) address. This numerical label (e.g. 24.139.99.226) helps establish your identity on a network. IP addresses can be static or dynamic, depending on the configuration of your network.
Leak: often used in the context of DNS, leaks are when the connection to a network via your VPN is compromised. As a result, data packets leak out and are no longer encrypted between you and your VPN service provider.
Logs/logging: all of your activities online, including requests for specific pages, are recorded on web servers. These records are called server logs and may be analyzed to establish patterns in your Internet traffic.
Network: a network, more specifically a computer network, consists of devices that use common telecommunications technology. These devices can communicate, share resources, and exchange files.
Obfuscation: to obfuscate is to purposely make the meaning of a message or communication difficult to understand. In the context of VPNs, obfuscation makes it “difficult” for your ISP to understand what you are doing on the Internet by concealing your online activity.
Packet: packets, network packets specifically, are units of data that are formatted to travel between networks. They include the IP addresses of the sender and the intended receiver, among other things. Everything you do on the Internet incorporates packets in one way or another.
Protocol: a protocol, or communication protocol, allows two or more devices to transmit information between them. They define the rules, such as syntax and semantics, for sending data between hardware devices or software.
Server: servers are computer programs or devices used to manage a network’s resources. They are often run on what is known as a client-server model, where a client requests the use of a program or another device that requires the server’s resources.
FAQs About VPNs
Can I stream with a VPN?
One of the most common activities people use VPNs for is streaming. In fact, many people use VPNs exclusively to stream content. This is mostly due to the geographical restrictions that streaming platforms place in other countries.
For example, the unofficial Netflix online Global Search (uNoGS) shows that the U.S. has access to a library of 5,887 titles from the Netflix catalog, but our neighbor Mexico only has access to 4,508 titles. Other countries, such as Sweden and Turkey, can access even less of the Netflix catalog, with 3,923 and 3,927 titles available, respectively.
Can I access the deep web with a VPN?
A VPN alone will not open the doors to the deep web. Accessing the deep web requires a special type of browser.
An example of this is the Tor Browser. Tor, derived from “The Onion Router,” is a free, open-source software that directs Internet traffic through a worldwide network of volunteers who host servers known as relays. As your traffic goes through Tor, it is encrypted and then anonymized. In the case of the Tor Browser, which is automatically programmed to use Tor, you also gain access to the deep web.
Accessing Tor with a VPN has one big advantage, namely, that it can conceal your usage of the network. Using Tor by itself does not do this. The most common method of doing this is known as Tor over VPN, where data first goes through your VPN service and then through Tor’s relays. This provides what is likely one of the highest levels of online security today.
You can find how to use Tor over VPN here.
Are VPNs legal?
In most parts of the world—including the U.S.—there are no legal repercussions for purchasing or using a VPN. Keep in mind that this does not absolve users from infringing copyright law or engaging in other illicit activities.
Interestingly enough, few countries outright ban VPNs through legislation. These include Iraq, Turkmenistan, Belarus, and the United Arab Emirates (for individuals, not banks and businesses). Beyond that, several countries such as China, Russia, Iran, and Oman ban VPNs that they do not sanction. And in other countries, like Turkey, VPNs are not banned per se, but the government disapproves of them and encourages ISPs to crack down on their use.








